Exploit Analysis Report: Know about the Helio Protocol Hack
Helio protocol, a liquidity protocol suffered an Oracle failure resulting the loss of approx $15.5M.
TL;DR
On December 02, 2022, the dumping of massive amount of aBNBc tokens on decentralized exchange opened the door for another exploit in which Helio Protocol was attacked and profited the attacker by approximately $15.5 million.
Introduction to Helio Protocol
Helio Protocol is an open-source liquidity protocol built on the BNB Chain that allows users to borrow and earn yield on the destablecoin $HAY.
Vulnerability Assessment
The root cause of the vulnerability is due to the failure of oracle in updating the price of the associated tokens after they had crashed to a significantly lower value than they earlier trading price.
Steps
The Ankr protocol had suffered a governance key compromise, allowing an attacker to mint massive amount of $aBNBc tokens. We have outlined the detailed analysis of the exploit in our blog post.
After the Ankr Exploiter dumped $aBNBc tokens, another user bought 183,885 $aBNBc tokens from 1inch for just 10 $BNB, which were worth about $2,879 at the time the event took place.
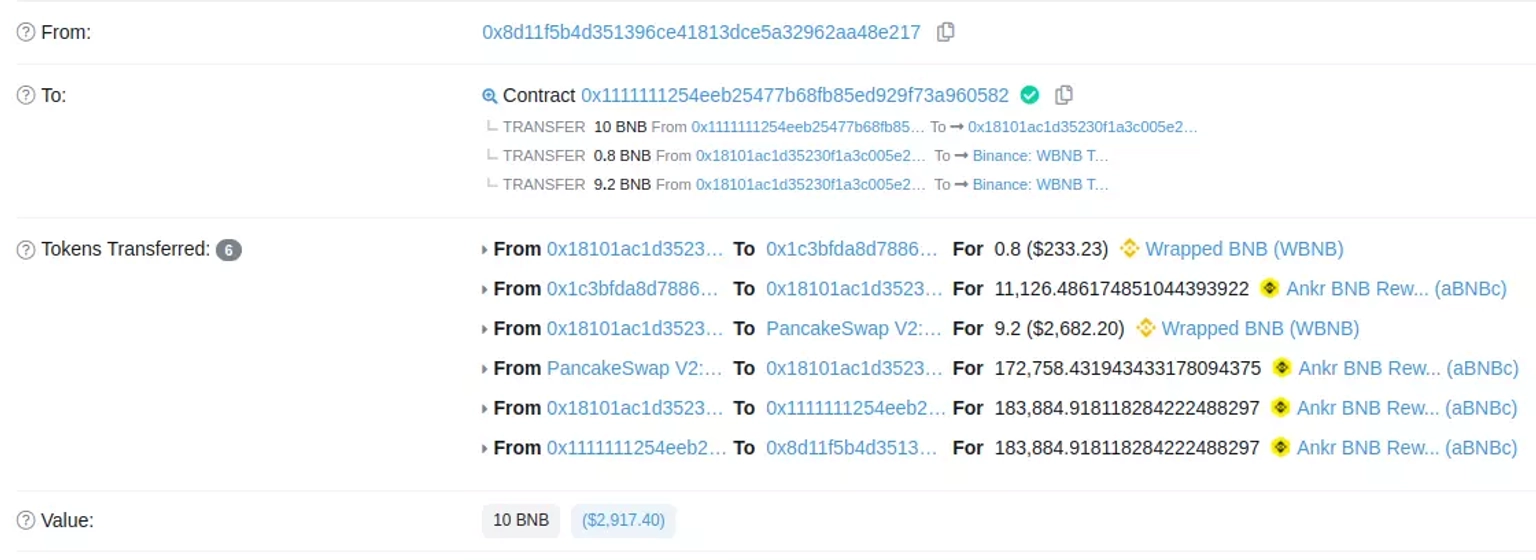
The attacker then deposited the 183,884 $aBNBc tokens into Helio Money to receive back 191,130 $hBNB tokens.
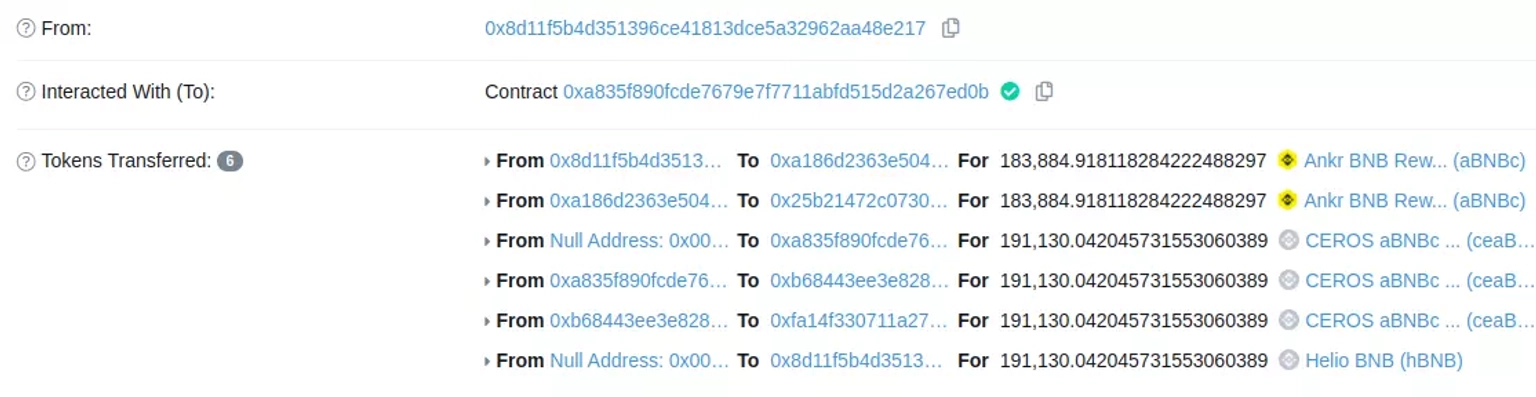
The price oracle of Helio was not updated during the exploit that took place with the $aBNBc tokens.
The attacker used the $aBNBc tokens they had already deposited as collateral to borrow 16,444,740 $HAY tokens.
The attacker then swapped 16,444,740 $HAY tokens to 15,504,986 BUSD.
The swapped BUSD is then transferred to this address involving three different transactions, and then to Binance hot wallet.
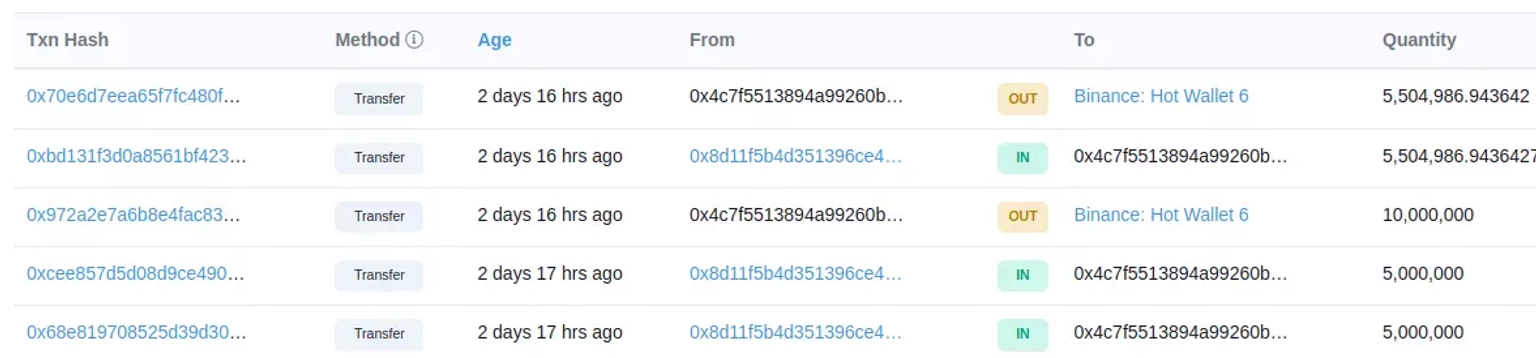
Changpeng Zhao, CEO of Binance also tweeted that the Binance exchange had frozen around $3 million of the funds that the hackers had moved to their CEX during this process.
Aftermath
The stablecoin $HAY de-pegged following the incident and fell to a low of roughly $0.21.
In a statement, the team explained that they were collaborating with Ankr Protocol to resolve the issue and that they had proposed a bilateral arrangement in which Ankr would pay for Helio's bad debt as a result of this exploit.
Additionally, in order to aid with the re-peg of $HAY, Ankr would be purchasing any extra $HAY that is produced as a result of the discounted $aBNBc and send it to a burn address.
How to Prevent Such an Attack Vector?
The vulnerability assessment points to a failure in the oracle's function, as it didn't update the price of associated tokens after they had experienced a significant crash in value compared to their previous trading prices. This vulnerability led to a sequence of events that allowed the attacker to exploit the system.
To prevent such attacks, the importance of robust price oracles like ChainLink is emphasized. While there is no foolproof solution, such oracles can significantly reduce the risk of price manipulation attacks.
In this context, the Helio Protocol's exposure to this oracle-based attack vector underscores the value of a dedicated cover pool within the Neptune Mutual marketplace. While oracle attacks typically aren't covered, exceptions can be made in certain cases. Users who purchase our parametric cover policies can claim payouts without the need for extensive loss evidence once an incident is resolved through the governance system.
Furthermore, recognizing that solely auditing smart contracts is insufficient, Neptune Mutual's security team extends its assessment to encompass DNS and web-based security, smart contract evaluations, and both frontend and backend security.
In conclusion, the Helio Protocol attack demonstrates the importance of proactive security measures within the DeFi ecosystem. Neptune Mutual emerges as a pivotal player in bolstering this security, offering a mechanism to mitigate the impact of vulnerabilities and fostering a safer and more resilient decentralized financial landscape.