Exploit Analysis Plantworld’s Flash Loan Attack Analysis Report
Plantworld $PLTD became the latest victim of a flash loan attack, due to flaw in transfer logic.
TL;DR
On October 18, 2022, Plantworld $PLTD became the latest victim of a flash loan attack, due to a flaw in transfer logic, resulting in a profit of 24,475 $BUSD for the hacker.
Introduction to Plantworld
Plantworld PLTD, a token operating on Binance Smart Chain (BSC) BEP-20, is a Plants-themed Blockchain game.
Vulnerability Assessment
The primary cause of this vulnerability is the hackers' ability to use a flash loan to reduce the balance of the PLTD contract in Cake-LP to 1 and then use the $PLTD tokens to swap all of the $BUSD into the attack contract.
Steps
Step 1:
The attacker address can be found here, alongside the attack transaction 0x8385625e9d8011f4ad5d023d64dc7985f0315b6a4be37424c7212fe4c10dafe0.
Step 2:
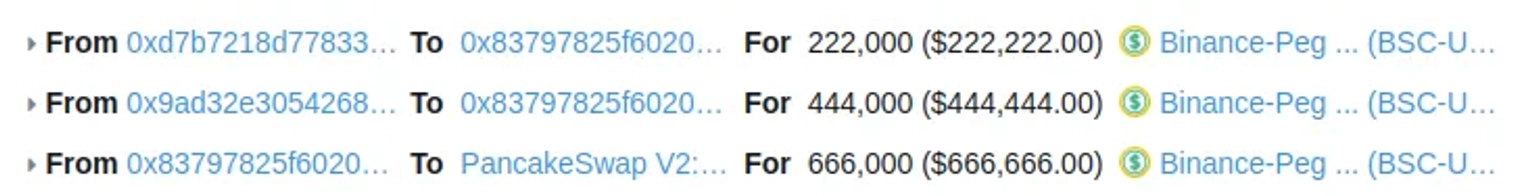
The hacker sent out two flash loan requests in order to withdraw 660,000 $BUSD.
Step 3:
The attacker then exchanged all 666,00 $BUSD for about 1.57 million $PLTD tokens.
Step 4:
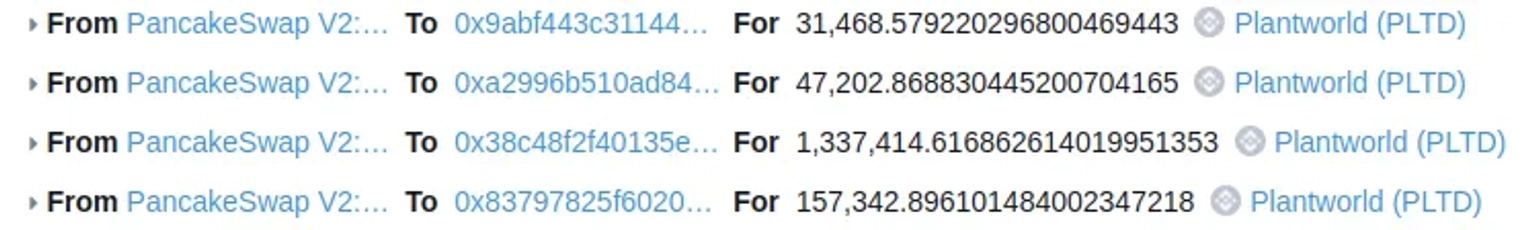
At this moment, the alleged hacker owned a significant amount of PLTD tokens, which will be utilized to manipulate the balance of PLTD token in Cake-LP.
Step 5:
As a pre-attack check, the attacker queries the current bron value and the PLTD balance of the Cake-LP.
Step 6:
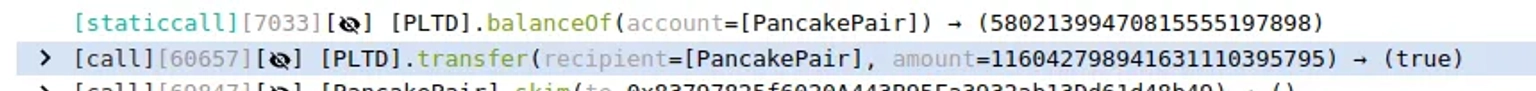
The attacker sends 116,000 $PLTD tokens directly to Cake-LP, which is precisely double the $PLTD token balance in Cake-LP from the previous step minus one.
Step 7:
When they call the Transfer function, the request is forwarded to the _transfer function. In this instance, the from address is the attack contract, takeFee is set to true, and the _tokenTransferSell function is then invoked.
Step 8:
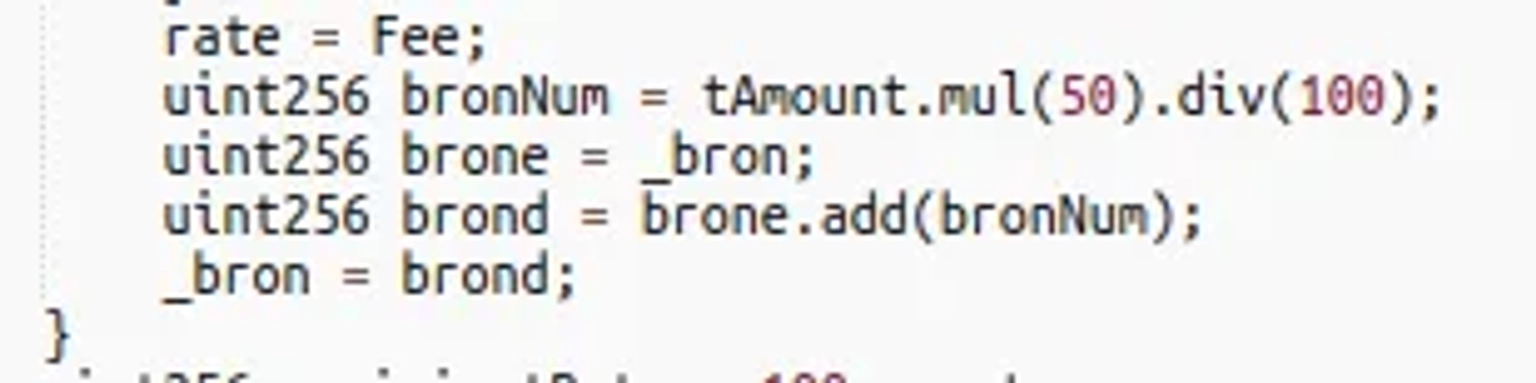
In the subsequent _tokenTransferSell function, the _bron parameter is set to half the transfer's number, which is equal to the Cake-LP balance minus 1.
Step 9:
The attacker utilizes skim to retrieve the PLTD previously transferred. If the from address is uniswapV2Pair in the _transfer function, _tokenTransferBuy is called.
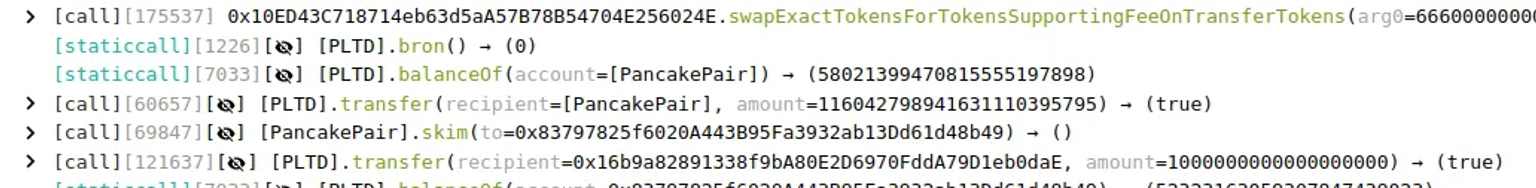
Step 10:
After _bron is initialized to the balance of Cake-LP minus 1, it further reduces the balance of Cake-LP to 1, and then calls the sync function of Cake-LP to synchronize the balance to reserve.
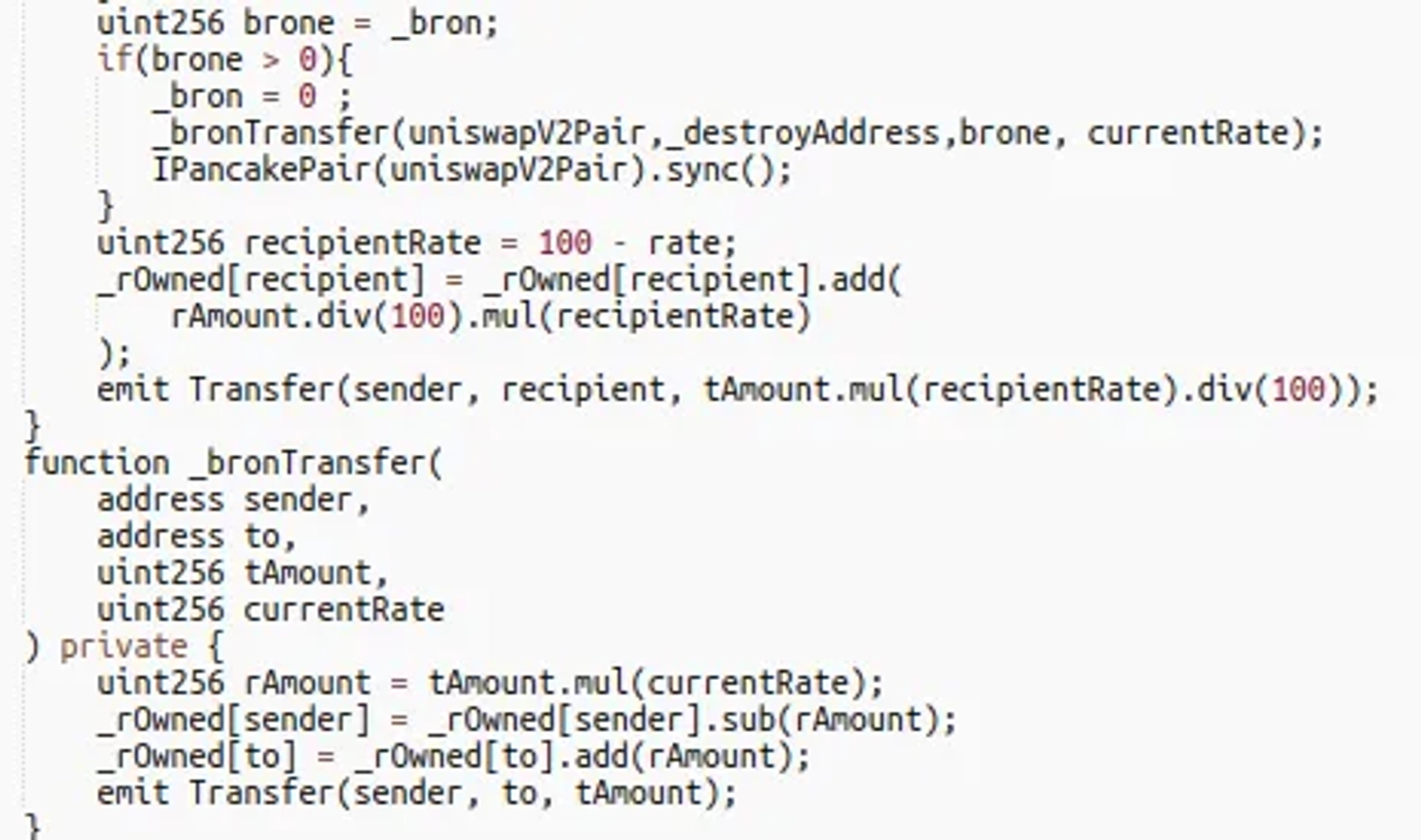
Step 11:
The attacker then exchanged all $PLTD tokens for $BUSD, nearly depleting the BUSD balance of Cake-LP.
Aftermath
The perpetrator obtained 690,000 $BUSD and repaid the 666,00 $BUSD acquired from the loan. The remaining profit of approximately 24,475 $BUSD is sent to this address 0x083c057221e95D45655489Fb01b05C4806387C19.
How to Prevent Such an Attack Vector
The absence of a protocol security audit can have catastrophic consequences for any crypto-native project. It is essential that the codebase be subjected to stringent auditing procedures to protect against such incidents to a greater extent.
It is also critical that the token balance of a directly operating pair in the same token contract be removed in the first place.