Exploit Analysis Decoding Sovryn’s Price Manipulation Vulnerability
Sovryn was hacked for approximately $1.1 million, in which the protocol lost funds from two pools.
TL;DR
On October 4, 2022, Sovryn was hacked for approximately $1.1 million, in which the protocol lost funds from two legacy lending pools; the RSK-bridged BTC (RBTC) pool valued at $900,000 and the USDT pool valued at $211,045 USDT.
Introduction to Sovryn
Sovryn is a permission-less, non-custodial smart contract-based system for bitcoin lending, borrowing, and margin trading built on RSK, a Bitcoin sidechain secured by the Bitcoin network. RSK's native token is RBTC, which is a 1:1 BTC peg.
Vulnerability Assessment
This vulnerability originated via a call to the _callTokensToSend function from an untrusted source.
Steps
Step 1:
The attack contract is first deployed by the preperatrator, who then transfers into 0.03 RBTC.
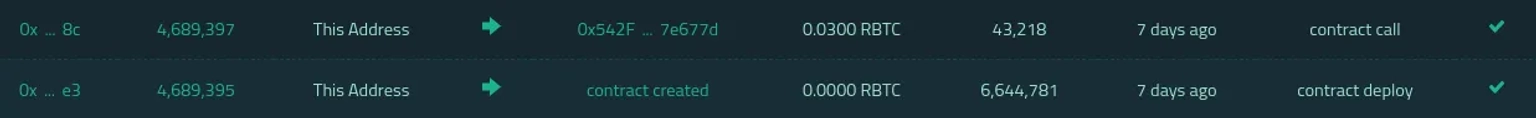
Step 2:
They then utilize the attack contract to borrow 8.20 RBTC to three pair addresses via flashloan before depositing the entire 8.23 RBTC. The attacker uses the LP to borrow 52,999 side tokens.
Step 3:
The closeWithDeposit function is then invoked to repay the collateral.
Step 4:
26,900 side tokens were swapped for 4.17 RBTCs. The attacker, on the other hand, minted 26,000 side tokens into 22,653 load tokens, but there is no mint function available in the closeWithDeposit function.
Step 5:
The attacker then used the side tokens to call the attack contract externally, and then called the mint function using the attack contract.
Step 6:
The tokenPrice function calculates the Load token price based on the number of side tokens, and the total number of tokens has not been updated at this time, resulting in the attacker receiving more Load tokens.
Step 7:
The attacker then uses the burn function to burn 22,653 Load Token in order to obtain 27,086 side token.
Step 8:
The attacker then loops through the related function to obtain the side token before converting it to RBTC.
Step 9:
The attackers then laundered the stolen funds to Tornado cash.
Aftermath
The system entered into maintenance mode after the developer realized the attack. It has been reported that half of the stolen money has been recovered, and the Treasury will reimburse the remaining losses in full. A later update revealed that all user funds that had become stuck on the ETH bridge had been released, with the exception of the user who was bridging in USDT to XUSD. The team's post-mortem on the exploit can also be found in this report.
How to Prevent Such an Attack Vector
One of the hardest things about discovering price manipulation attacks is figuring out how the different smart contracts in a transaction interact with each other. Price manipulation occurs from logical flaws in DeFi applications, so finding it requires looking at multiple smart contracts and understanding the high-level semantics of DeFi applications. There is no silver bullet when it comes to price oracles. However, oracles like ChainLink can help stop price manipulation attacks to a greater extent.