Exploit Analysis Decoding GMX's Price Manipulation Exploit
GMX was the victim of a $565,000 price manipulation exploit on the AVAX/USD pair.
TL;DR
On September 18, 2022, GMX was the victim of a $565,000 price manipulation exploit on the AVAX/USD pair.
Introduction to GMX
GMX is a decentralized spot and perpetual crypto exchange, powered by Artibitrum and Avalanche, that supports low swap fees and zero price impact trades.
Vulnerability Assessment
In a price manipulation attack, an attacker manipulates the token price of the susceptible DeFi app. There are two forms of these attacks: direct and indirect price manipulation, which have become more prevalent with the advent and growth of DeFi, DEX, and lending applications. The attacker uses an unwanted trade on the DEX to directly affect a token's price in the liquidity of an AMM in a direct price manipulation attack. However, in the latter approach, a trade on an AMM is used to subtly affect the token price of a vulnerable DeFi application, whose price mechanism depends on real-time status. If a lending app's price system is manipulable, a borrower may take out more tokens than they are eligible to borrow.
Steps:
Step 1:
GMX advocates the zero slippage of perpetual trades as their primary strength, and has a fixed price for assets fed by an oracle. If a trader long or short any size on GMX, there is no price impact.
Step 2:
The profits are liquidity provided by $GLP token holders. Users swap crypto native tokens or stable-coins for GLP tokens on the GMX dex. When traders generate profits, liquidity providers incur losses. Therefore, when traders exploit this vulnerability, GLP holders may lose all their money.
Step 3:
This trader took both a long and short position on GMX without affecting the price, then impacted the price on CEX to manipulate the oracle price feed.
Step 4:
In doing so, he successfully extracted profits from GMX's AVAX/USD market by opening large positions with no slippage and then moving AVAX/USD in their favor on other venues. As he switched from long to short 5 times, he created a sinusoidal pattern that lasted over an hour.
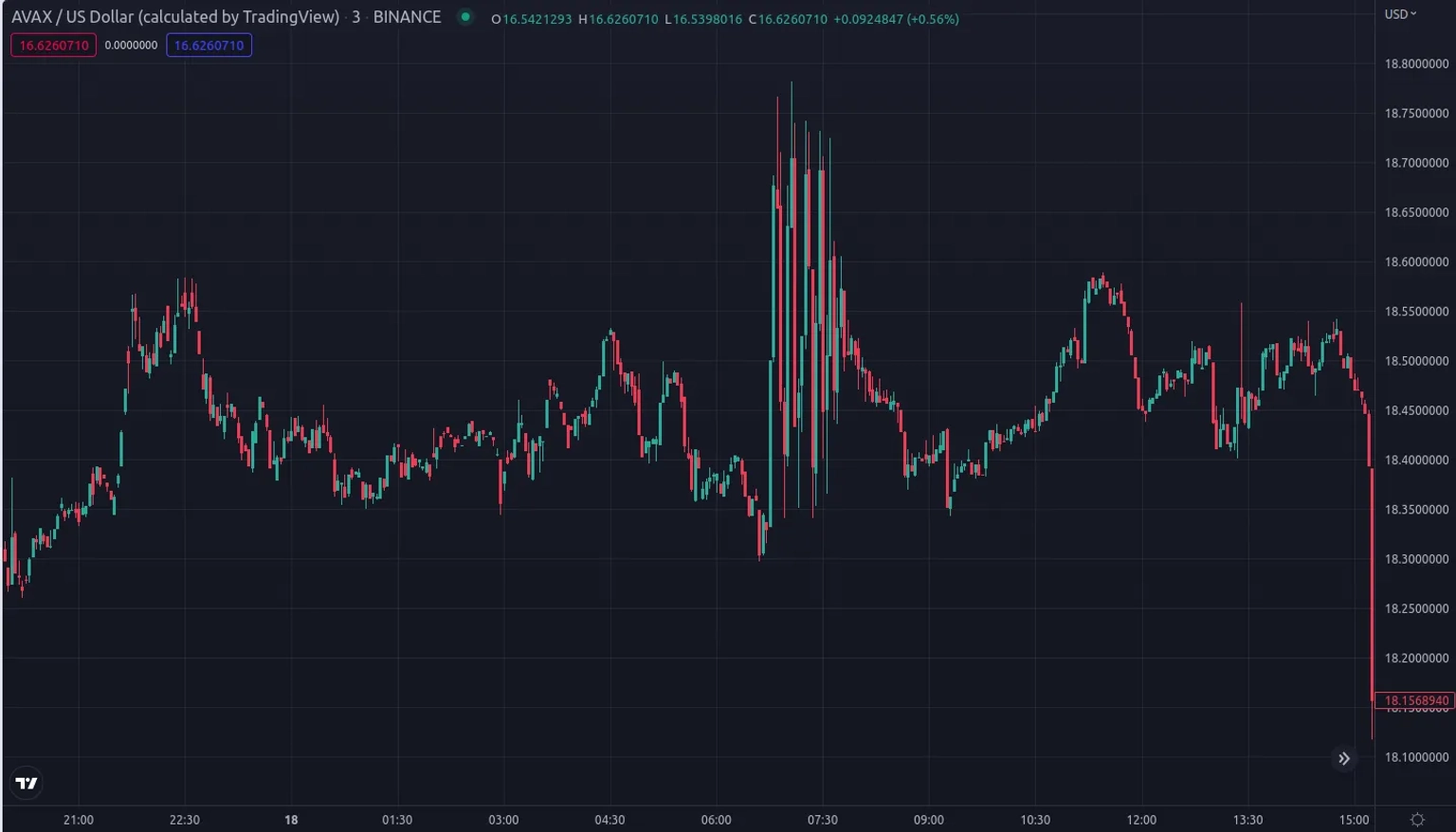
Step 5: In the first cycle, he made approximately $158k by trading clips of $4-5 million at a time. The trader repeated this process five times to profit between $500,000 and $700,000. A part of this profit was also distributed to market-makers on other trading platforms in order to move the price of AVAX. Step 6: Given the design framework used to deploy the workings of GMX, the trader essentially executed large trades against GLP holders with zero slippage, at the oracle price, and without taking into account any price impact. A skillful trader could have used price manipulation to siphon all the liquidity from GMX due to no price impact.
Aftermath
To prevent the exchange from such exploitation, the team later capped the short and long-open interest for AVAX. Open interest for AVAX long perpetual futures has been set at $2 million, while open interest for AVAX short perpetual futures has been capped at $1 million. The GLP and GMX markets continue to operate normally.
Prevention against Price Manipulation Attack
Price manipulation originated from the logical flaw in DeFi apps, so spotting it necessitates a thorough examination of numerous smart contracts and a comprehension of their high-level semantics.
Protocol, and Platform Security
Our security team at Neptune Mutual can validate your platform for DNS and web-based security, smart contract reviews, as well as frontend and backend security. We can offer you a solution to scan your platform and safeguard your protocol for known and unknown vulnerabilities that have the potential to have catastrophic long-term effects. Contact us on social media if you are serious about security and have the budget, desire, and feeling of responsibility to do so.
By Neptune Mutual